Nuremberg Nonsense
Mark Honeychurch - 28th February 2022
Although Bronwyn’s put together this week’s newsletter, I couldn’t help myself and wrote a small piece about the protesters’ obsession with Nuremberg.
The image above shows some of the less savoury attendees at the Freedom Protest at parliament. Many of them have views that are horribly racist, and some of these people have been calling for the overthrow of our government. A word that is often used by these people, and other protesters, is Nuremberg. So, what’s going on with this? What’s Nuremberg, and why do these people think it is relevant to our government?
After the end of the second World War, the allies ran a court in Nuremberg, Germany to prosecute German war criminals. At the end of the Nuremberg Trials, several defendants were acquitted, seven were given custodial sentences and twelve were given the death sentence (although only ten ended up being hanged to death).
After the trials, a set of guidelines were written covering some of the unethical medical experimentation that the Nazis had performed - called the Nuremberg Code. This code has been the basis of medical laws in several countries, although the Code itself is not part of law in any country.
So, what does this have to do with the protesters at parliament? Well, since the beginning of the pandemic, with the lockdowns and face masks, and now the vaccine and mandates, some of those who have been unhappy with our response to COVID have been talking about how our leaders have breached the Nuremberg Code, and that as such they need to be held accountable. Given that the Nuremberg Trials ended with ten people being hanged, some people think that this sentence is appropriate for members of our government, and that a court needs to be set up to allow for prosecution and sentencing - a court presumably run by the protesters. Let’s look at one of these protesters, and what he’s been doing…
A fresh group of protesters turned up in Wellington this weekend by boat from the South Island. One of them, Daniel Suter, told the NZ Herald that he saw a dolphin during the crossing and took it as a sign - “In a way, it’s a symbol of freedom. No one’s telling them to get a jab.” Now, Daniel is a “web developer” - you’ll see soon why I’ve used scare quotes around this description. Daniel has recently built a website to manage a list of those who should be prosecuted for their supposed crimes, at https://www.nuremberg.nz/.
The website states (the bold text and fixing of bad grammer are both mine):
“After the second world war the Nazi war criminals were tried. Notably the argument “I was just doing what I was told”, was not a valid excuse… In New Zealand, our basic human rights are being trampled on, because of a virus with a similar mortality rate to the seasonal flu. The excuse is that all these human rights violations are for our own safety. Coercion from Politicians and Media have resulted in more than half the population of Aotearoa being bullied into taking an experimental injection for which the long term side effects are completely unknown… It is therefore our belief here at Nuremberg.nz that those responsible for multiple breaches of The Nuremberg Code 1947, The Helsinki Declaration 1952, The UNESCO Declaration on Bioethics and Human Rights, NZ Bill of Rights 1990 will ultimately have their day of reckoning.”
The Accused page of the website has a list of MPs, scientists (including skeptic Siouxsie Wiles) and even staff from organisations like Mitre 10 and Tennis Auckland (presumably for their mask policies) who are considered to be violating people’s human rights with their public health measures, along with a voting system allowing people to upvote those they feel are most worthy of being put on trial.
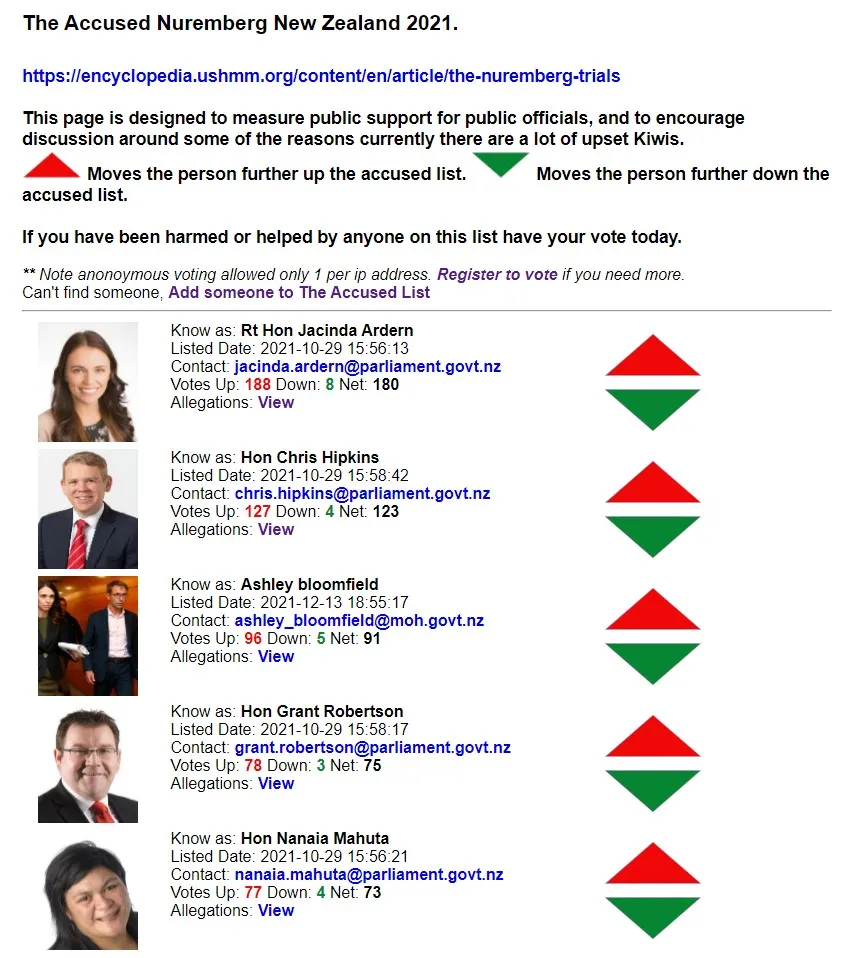
Now, I’m sure it won’t surprise you all to hear that this website, as well as being sickening, is also very badly coded. Without going into details, although Daniel might call himself a web developer I’d say that it might be more accurate to call him a dangerous amateur - dangerous in that it’s obvious he has no idea how to implement proper security in a PHP/Javascript website.
Interestingly, Daniel has also built the website for anti-vaccine lawyer Sue Grey - suegrey.nz. When I found this out today and visited the site to see what security issues were there, I wasn’t too surprised to find that someone’s beaten me to it… and put their findings to good use.
Sue’s website has a few articles, such as this one about masks. Now, for anyone who has already clicked on that link, I have to apologise - you’re probably thinking right now that I just RickRolled you. For everyone who didn’t click the link, I can tell you that it takes you to a Rick Astley music video. If you’re not in the know, here’s what Wikipedia has to say about this internet phenomenon:
Rickrolling or a Rickroll, is an Internet meme involving pranking an unexpected appearance of the music video for the 1987 song “Never Gonna Give You Up,” performed by the English singer Rick Astley. The meme is a type of bait and switch, usually using a disguised hyperlink that leads to the music video.
The URL that I used above is not a link to the video, though, it’s an actual URL on Sue Grey’s website:
https://suegrey.nz/articles/140041/To-Mask-or-not-to-Mask?
So why does it send you to the infamous Rick Astley music video? Well, each article has a comments section at the bottom, for people to leave their thoughts on the article. And the website will take whatever you type in the comments section, and save it to a database. From then on, your comment will be loaded whenever anyone loads the article in their browser. And Daniel has been kind enough to allow HTML tags (like <p> and <bold>) to be saved and loaded here, presumably so that people can make their comments look pretty by making them italic, coloured, etc.
However, as the site allows any and all content in the comments, one of the HTML tags you can use is the <script> tag, and this lets you add Javascript (computer code) to the article’s web page. This is what someone appears to have done to Sue Grey’s website. We can see the source code of the page in Chrome via this URL:
view-source:https://suegrey.nz/articles/140041/To-Mask-or-not-to-Mask?
Now, when I did this today, I found exactly what I thought I’d find in the comments section of the page - a comment added by a user called “haha”. Here are the contents of their comment:
It’s not very long, is it? All this does is tell the browser to run the text inside the <script> tags, and that code then pushes a new URL to the Address Bar in your browser. location.href is a variable that controls what the current page is, and this code sets it to a new URL (with the =), in this case to a string (a piece of text) that is the address of the Rick Astley video. So, whenever this comment loads on the page in your browser, this tiny piece of code runs and tells your browser to jump to the Rick Astley video URL. I have to applaud whoever took the time to add this particular comment to this and other articles on Sue Grey’s website!
On a more serious note, a vulnerability like this can be used as part of a Cross Site Scripting (XSS) hack to capture someone’s login details, cookies and more. On top of this, I have a sneaking suspicion that Daniel’s PHP code is probably vulnerable to another type of attack called a SQL Injection, where commands can be sent through the website to its backend database to delete or steal data.
As much as I find it sickening that there’s a New Zealand website calling for a kangaroo court to convict (and potentially murder) MPs and scientists, with 188 people voting for our prime minister, at least there’s hope that the person who has created this site is probably known to the Police. I also figure that whoever the Police use for monitoring extreme content online wouldn’t find it very hard to scour the site for content that is supposed to be hidden from users, content that might be of use to keep track of some of the more violent and angry protesters. Honestly, from my brief look into the website today I can tell you that the site leaks data like a sieve.